京东云 WAF SQL 注入
前提背景:这是京东云客户云骊的 web 服务,其中上了京东云的 waf,正常访问
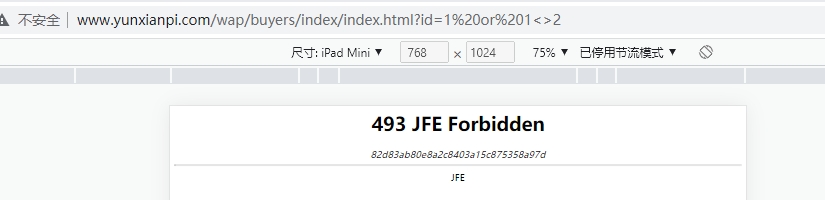
http://www.yunxianpi.com/wap/buyers/index/index.html当我在 url 中加上一段 sql 注入代码 ?id=1 or 1<>2,这段参数条件就是不管什么 sql 语句 where 后面条件都为真
http://www.yunxianpi.com/wap/buyers/index/index.html?id=1%20or%201%3C%3E2返回京东云 493 Forbideent 已经被京东云 waf 拦截了
京东云 waf 后台查看攻击日志
攻击详情
GET /wap/buyers/index/index.html?id=1%20or%201%3C%3E2 HTTP/1.1
Host: www.yunxianpi.com
Connection: keep-alive
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (iPad; CPU OS 13_3 like Mac OS X) AppleWebKit/605.1.15 (KHTML, like Gecko) CriOS/87.0.4280.77 Mobile/15E148 Safari/604.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: language=zh; subsite_id=0; subsite_name=%E5%85%A8%E9%83%A8; site_id=84; site_name=%E5%A4%A7%E4%B8%8A%E6%B5%B7%E5%9C%B0%E5%8C%BA处置详情,动作为 Block
waf:sdk:10087->block((10087:1 or 1<>2))||->().参考文章
https://docs.jdcloud.com/cn/web-application-firewall/step-3
Last updated